|
|
|
CXO Voices
The monthly newsletter for CXO REvolutionaries
Nicole Darden Ford VP & CISO, Global Carrier
|
 |
|
|
|
|
 |
By empowering people with authority, resources, information, and accountability, and then investing in them, individually, you'll see a dramatic change, a transformative change.
|
 |
|
Nicole Darden Ford, VP & CISO, Global Carrier

|
|
|
|
|
Nasdaq modernizes boards; Women in IT Executive Conference - EMEA event announced; CXO REvolutionaries forum goes live
Christopher Jablonski, Editor-in-Chief, CXO REvolutionaries
Nasdaq’s new SEC-approved requirement for its listed companies to enhance diverse boards acknowledges the link between diversity, equity and inclusion (DEI) and better financial performance and corporate governance. The move is not just a leap forward for investor confidence and transparency, but spells progress for equitable representation among circles of power and influence.

With the EMEA edition of the Women in IT Executive Conference coming up next month, we’re excited about our progress with DEI and playing our part in leading the tech and cybersecurity industry forward. At the inaugural edition last summer, REvolutionary and VP and CISO at Carrier, Nicole Darden Ford shared her wisdom about equity and equality to inspire future leaders and board members. You can watch her session and the entire event on demand. And join our Women in IT Exec community on LinkedIn and in the CXO REvolutionaries forum.
Speaking of the forum, we celebrated the official launch and are welcoming new members. Learn more.

|
|
|
From the Office of the CTO:
Use SASE to get network visibility through daily ops reviews
Pam Kubiatowski, Sr. Director, Transformation Strategy/Field CTO - AMS, Zscaler
Security requires daily vigilance. As part of a proactive enterprise IT security strategy, you need to know what is happening in your network, how, where, by whom, and when. These day-to-day network statistics hold important security data—but often aren’t used to make IT security decisions.
A daily network operations review can provide security gatekeepers deep insights to what is happening (and what shouldn’t be happening) in the network:
 |
What data is moving through your network? Seeing what applications are accessed by what devices provides a good traffic pattern picture. Sudden changes to overall patterns can show malicious infiltration that has breached security.
|
 |
Where is traffic traveling on your network? Knowing normal traffic data flow patterns highlights sudden changes in origins and destinations. New or unexpected dataflows could be a sign of malicious intent.
|
 |
How much bandwidth is getting used? Understanding normal bandwidth usage throughout the day unmasks unexplained changes. Sudden increases during “slow” hours or from generally low-use sources could mean a breach.
|
 |
Who is accessing what applications? Knowing which users normally access which areas of the network Detecting a sudden change in the access profile of “UserA” could be a sign of a compromised login.
|
 |
When is access requested? Recording when “UserA” typically shows network activity is crucial to understanding your network. Sudden patterns that don’t match UserA’s general work hours could be a sign of a compromised login.
|
Getting this level of network visibility across the entire network can be challenging—especially as more and more applications, data, and users sit outside legacy “castle-and-moat” architectures.
A SASE security posture can help provide you with the metrics you need to make good decisions on policies, postures, and initiatives.
|
|
|
5G & zero trust: An introduction for CXOs
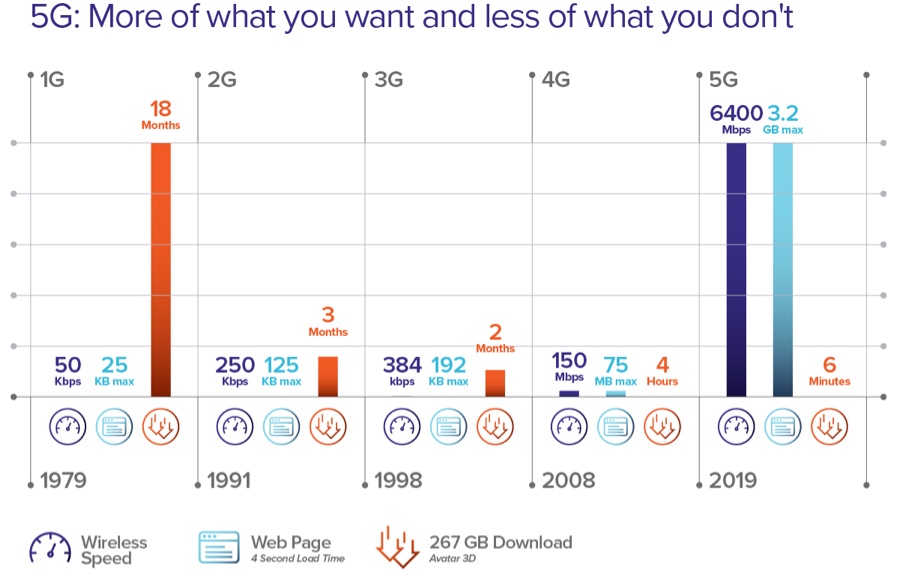
With 5G, virtualized, highly distributed workloads are possible with some residing in MEC-based edge platforms.
“I’m most excited about the exponential expansion of new devices and applications that will eventually come from 5G. However, this creates a broader attack surface, which is why we work with companies like Zscaler who have the best solutions in the industry to protect users in the 5G world,” says S. Jay Lawrence, General Manager of Technology Enablement, SuperMicro Computer, Inc.
Widespread 5G in the enterprise is on the horizon and to help our community of leaders like Jay Lawrence get ready, we published a guide by Dr. Ken Urquhart, Global VP of 5G Strategy. It spells out the opportunity, key considerations, and decisions that every IT and security leader will face sooner or later.
Read now.
|
|
|
Staff Picks and Events
 |
Dark Reading: A CISO’s perspective on ransomware payments
How living through the experience of assisting a small business with a ransomware attack changed a Zscaler CISO’s perspective on whether to pay.
Read now
|
 |
You Need Deception Technology.
And It’s Not Why You Think
Cyber deception is the missing piece of the defensive security puzzle and can give your security operations center the upper hand. Discover how it can and should be used to the fullest potential and can cause an attacker to second-guess everything they think they know about your environment.
Read now
|
 |
ThreatLabZ June 2021 report: Deconstructing Kaseya supply-chain attack and the Minebridge RAT campaign
Taking a cue from marketers, Malware such as DoppelPaymer rebranded itself to avoid detection. ThreatLabZ analyzed this along with enterprise IoT vulnerabilities, how Joker keeps propagating in Google Play, and a new variant of Netwire RAT targeting government organizations.
Learn more
|
 |
How leaders cultivate coherent change
In his first contribution to CXO REvolutionaries, Howard Sherrington, Director of Transformation Strategy, shares key lessons on leading coherent transformation through change, and creating a framework for communication, interdependencies, and culture. All of this in the context of his experience implementing zero trust at the BBC.
Read now
|
 |
CIOs and CISOs: from strange bedfellows
to power couple
Moderator and CIO Les Ottolenghi recently spoke with former BMW CIO
Klaus Straub and former financial industry CISO
John Meakin about how digital transformation, innovation, and security require alignment between the CIO and CISO, especially when it comes to governance, compliance, and risk.
Listen now
|
 |
New & Notable from Zenith Live 2021
On this episode of Cloudy with a Chance of Trust, Lisa and Pam discuss the most interesting things they heard at Zenith Live 2021 this summer - innovations, customer insights, and more - plus how to access the conference presentations on-demand.
Listen now
|
 |
Reducing the Risk and Complexity of Secure Cloud Deployment - Japan (September 10th, 3PM JST)
The race to the cloud introduces risks, including cybersecurity gaps, misconfigurations, and vulnerabilities. Learn from those who’ve done it and watch an expert deconstruct a data breach, offering best practices for your cloud security management.
Learn more
|
|
|
|
|
|