|
|
|
CXO Voices
The monthly newsletter for CXO REvolutionaries
Phil Armstrong, President & CEO of Macanthium Ventures Inc.
|
 |
|
|
|
|
 |
In today’s fast-paced world, human error and distraction are emerging as our biggest threats. Criminals have increasingly sophisticated tools, and it takes increasingly sophisticated solutions to deliver on our security promises.
|
 |
|
Phil Armstrong, CXO REvolutionary, President & CEO of Macanthium Ventures Inc.,

|
|
|
|
|
Embrace digital, or get disrupted
David Avery, Transformation Analyst, Zscaler
The pandemic accelerated IT’s adaptation of infrastructure to meet rapid change. As the world recovers, we’re seeing a new hybrid work model: some people working from home, some in the office, and many mixing and matching between the two. IT’s ability to control devices, locations, and connections is a luxury of the past. Now, teams must oversee people working from anywhere, using non-corporate devices, and accessing apps and assets in the cloud via direct internet connections. CXOs need to execute a strategic vision that makes the most of this new paradigm or risk disruption from others who do.
Former Great-West Life CIO and current CXO REvolutionary Phil Armstrong knows as much as any IT leader about moving large corporate infrastructures into the digital age and securely leveraging the cloud for better organizational agility. Recently, on CXO REvolutionaries, Phil discussed the importance of not "saving face" as an IT leader, explained how CIOs navigate a "perfect storm" of technology and change, and how to raise the "anchor of legacy debt" in order to move into the future.

Phil also joined Head of Transformation Strategy at Zscaler, Dan Shelton, in the inaugural episode of The CIO Evolution podcast, which highlights how enterprise CIOs plan and upgrade their legacy networks, the financial and operational transformation challenges they’re facing, and what security measures are needed in the new work-from-anywhere, mobile- and cloud-based world. Listen now
|
|
|
From the Office of the CTO:
Don’t forget to measure OPEX savings when planning
Companies making the case for cloud-based zero trust architecture (ZTA) typically use ROI calculations that focus on CAPEX: what equipment can be eliminated, replaced, or not even purchased in the first place? (Answer: legacy VPN and security appliances.) Switching to ZTA eliminates the upfront cost of those devices. Is that enough to justify a ZTA investment? For most enterprises, probably. But there are efficiencies to be gained by eliminating the hidden OPEX costs associated with operating legacy appliances.
Operating within a legacy environment is inefficient: How much time do IT administrators spend writing the same access policy in multiple languages for data center firewalls, AWS security groups, Azure access controls? How many log formats does IT have to correlate to really understand what happens to user traffic accessing a remote application? How much time is spent updating software across all security stacks in all offices?
|
Zero trust architecture in the cloud eliminates OPEX costs:
|
 |
With ZTA, internet-bound traffic travels directly over local providers using zero trust identity-based management, supplanting the need for MPLS networks (and the cost and performance-degrading backhauling associated with them).
|
 |
In a ZTA environment, direct, seamless application access improves performance, reducing user complaints and thus IT support costs.
|
 |
Using the Zscaler Zero Trust Exchange eliminates the administrative overhead of security-stack patching, maintenance, and upgrading.
|
|
|
|
What F1 cars can teach us about
5G and top speed
“If 3G is a Volkswagen Beetle, 4G is a Porsche. 5G is the Millennium Falcon,” writes
Nathan Howe, VP, Emerging Technology at Zscaler. In his latest analysis, Howe points out that a combination of high-tech innovations allow F1 race car drivers to push the limits and 5G works in a similar way. Open standards and advancements like Multi-access Edge Compute (MECs) enable virtualized, highly distributed workloads with low latency. Widely touted 5G speeds, however, are only possible in the best conditions, and overall performance in an enterprise will be determined by how IT fine-tunes infrastructure, services, and security.
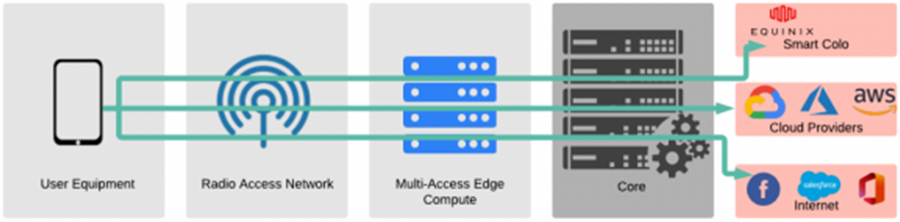
With 5G, virtualized, highly distributed workloads are possible with some residing in MEC-based edge platforms.
Howe urges IT leaders to use 5G as an opportunity to reconsider their security strategy and embrace inline security and local internet breakouts so that employees can be productive with secure, fast access to internet and cloud resources.
Read more
|
|
|
Editor's Picks and Events
 |
Legacy cybersecurity is an albatross:
Digital success needs a better model
The security market is growing exponentially, but is it growing with the right solutions? How should we approach cybersecurity, legacy infrastructure, and user experience?
Rohit Adlakha, CXO REvolutionary and former Chief Digital & Information Officer and Global Head, Wipro HOLMES™ recommends zero trust.
Read more
|
 |
From Wisconsin’s former CIO:
Cybersecurity must be a national priority
“My plea to CIOs is to look for vendors and partnerships that scale and provide a complete cyber defense quickly. Evolve.” CXO REvolutionary
David Gagigal says recent cyberattacks on public infrastructure is a wake-up call.
Learn more
|
 |
ThreatLabZ June 2021 report: Deconstructing Kaseya supply-chain attack and the Minebridge RAT campaign
The Zscaler ThreatLabZ security research deconstructed the new Kaseya VSA supply-chain attack and took a deep dive into the Minebridge RAT infection chain.
Learn more
|
 |
Productivity, Efficiency, and Speed: Why Digital Experience Matters [Event Recap]
Episode 3 of the Zscaler Virtual CXO Summit focused on making the digital experience for end users smooth, available, and as fast as possible all while delivering powerful zero trust cybersecurity.
Read the takeaways and watch on demand:
AMERICAS |
EMEA
|
 |
Aug 11: Reducing the Risk and Complexity of Secure Cloud Deployment (APAC)
The race to the cloud introduces risks, including cybersecurity gaps, misconfigurations, and vulnerabilities. Learn from those who’ve done it and watch an expert deconstruct a data breach, offering best practices for your cloud security management.
Learn more
|
|
|
|
|
|